Secure Remote Access & Privileged Connectivity: Beyond VPNs
Remote work is permanent — but legacy VPNs were never designed for today’s threat landscape.
The VPN Problem
Traditional VPNs:
Grant broad network access
Trust devices after login
Create large attack surfaces
Are prime targets for credential theft
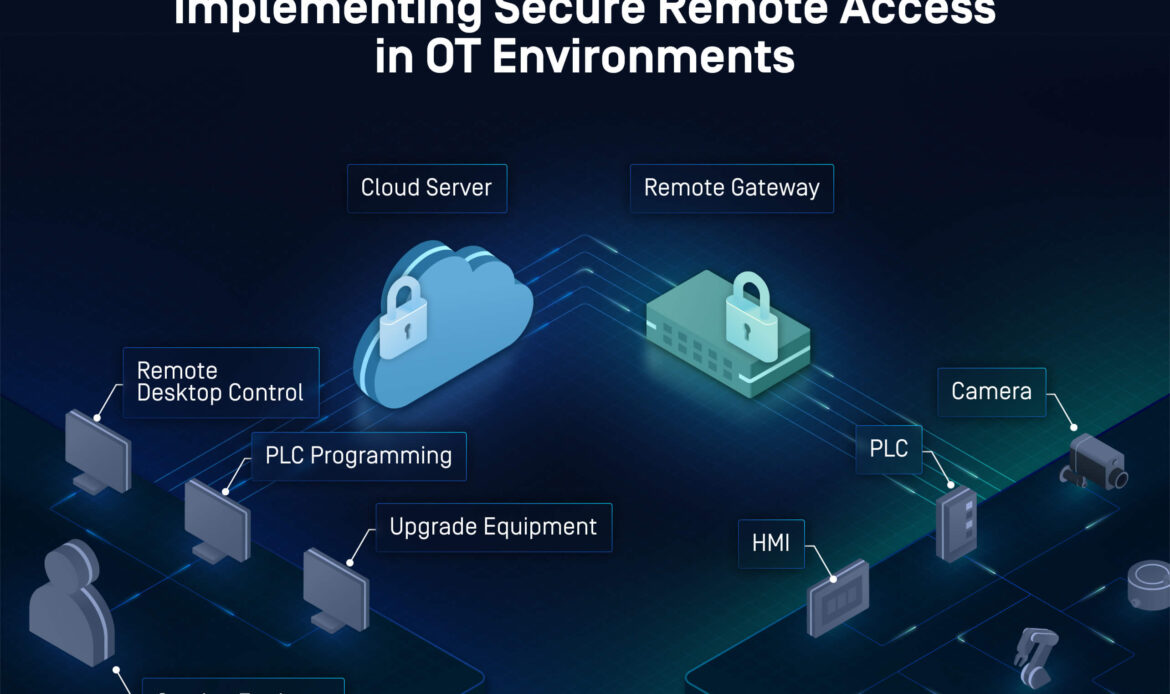
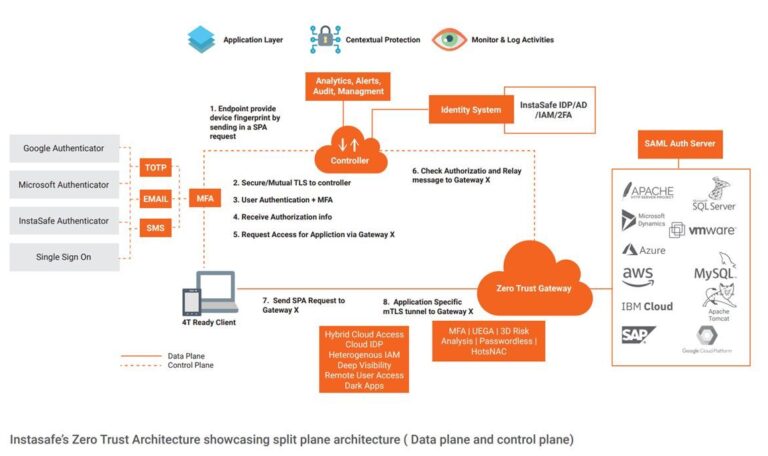
Zero Trust Network Access (ZTNA)
ZTNA replaces VPNs with:
Identity-based access
Application-level connectivity
Continuous verification
Device posture enforcement
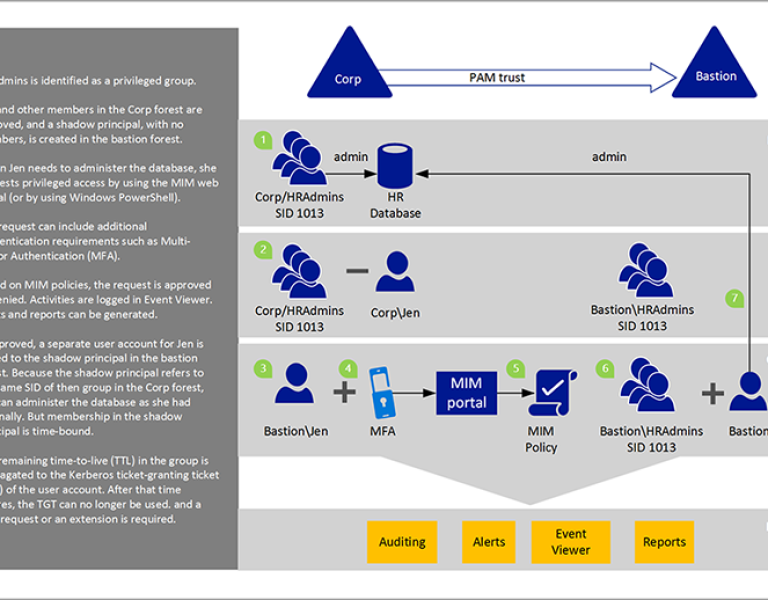
Privileged Access: The Crown Jewels
Administrator accounts are the most targeted assets. Privileged Access Management (PAM) ensures:
Just-in-time access
Session monitoring
Credential vaulting
Auditability
Final Thought
Remote access should reduce risk — not extend it.